WPA2 KRACK Vulnerability Exposed
RIP WPA2 16 October 2017 ?
Will WPA2 be replaced by WPA3 or simple being patched?
The vulnerability explained:
IT Security Expert from Belgium Mathy Vanhoef show how a black hat hacker could easily intercept and sniff data transmitted from a wireless device can be a IoT.
Android or a laptop by exploiting a new vulnerability found in WiFi Authentication used in WPA2.
The hack took Mathy about 4 minutes to execute and it might be less.
KRACK vulnerability read sensitive data
Mr. Vanhoef described the vulnerability as KRACK Key Reinstallation Attack explained that attackers can exploit this vulnerability to read data being sent between a device and wireless access point it is connected to.
Even if there is being utilized the strongest WPA2 WiFi encryption.
WPA2 Security Broken and vulnerable to attack
KRACK Vulnerability exploits a weakness in WPA2 WiFi Protected Access Version 2 the standard of WiFi Security encryption protocol that most
endusers, organizations, businesses, government deploy today to protector their WiFi networks.
Find out if you are open to WiFi Vulnerability Attacks
WiFi Networks by the millions vulnerable to KRACK vulnerability
The vulnerability is categorized as high severe and can be abused by black hat attackers to steal sensitive information from WiFi encrypted networks
that earlier was believed to be secure.
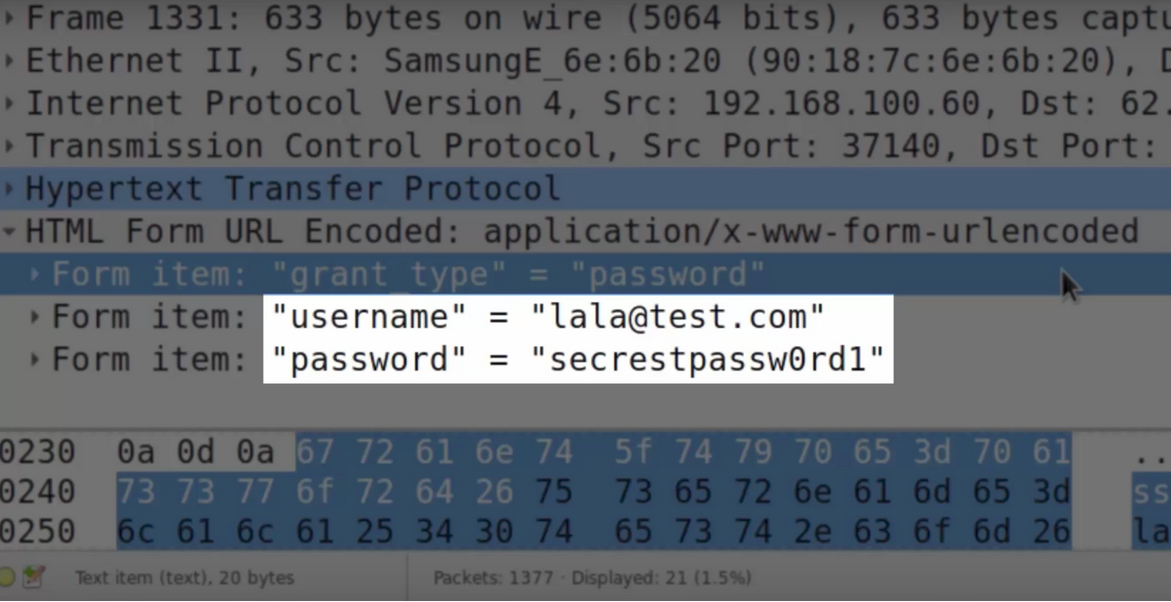
The information is not limited to and includes chat messages, emails, images photos, passwords, credit cards, sensitive personnel data.
The attack can exploit all modern unpatched WPA2 protected WiFi networks.
This will count networks in the millions to be vulnerable if not being
secured and patched.
Not only limited to eves dropping also injection
As it is not bad enough that attackers can eves drop the traffic they can also inject and manipulate data.
This way attackers can inject Malware, Ransomware, worms into website traffic and easily infect users which believe they are secure.
What is important to know about the KRACK vulnerability?
What can you do about this KRACK WPA2 Vulnerability?
Immediately update all your connected devices including laptops, smart phones, tablets, routers, IoT.
Likely they will receive popup about new security patches that you can easily install.
All major vendors have already told patches are on the way.
Including Microsoft, Apple, Google, Android, Cisco, Linux distributions, OpenBSD, FreeBSD and other non listed systems.
Android and Linux most vulnerable to CRACK WPA2 Vulnerability
The most easily exploited by the vulnerability is Linux and Android devices according to Mr Vanhoef.
Google is already on high alert to have patches ready for all devices as fast as possible.
A general problem with Android operating system is that many users are not aware about they must install security updates.
There can also be different time for Android vendors to push out patches.
It is recommended to keep watching your devices if they have not already been upgraded.
If no patch is coming for your device it would be recommended to replace it with another device or disable WiFi usage.
Patches for popular Linux systems are already available for download.
Some security experts claim that KRACK might be rare on Windows or iOS devices still Microsoft and Apple has released patches.
What is the real life risk to KRACK WPA2 Vulnerability?
The Security researcher has been very responsible and disclosed the vulnerability to vendors very early for them to develop patches.
The exploit tool it self has not yet by the writing of this article been released.
It might be released or leaked in the future.
Users must always use HTTPS to prevent sniffing of sensitive data even when the WPA2 encryption is being broken.
Also only visit trusted websites to prevent malware attacks.
|