Find out more with the Infographic below.
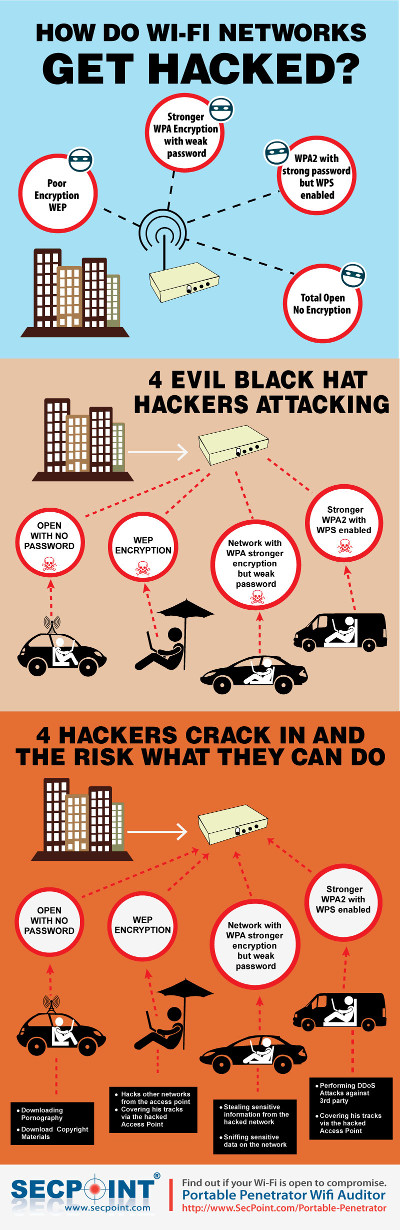
Learn how attackers easily break into WiFi networks and compromise the keys.
The Infographic explains step by step how attackers break into the different types of network encryption.
Ranging from WEP , WPA, WPA2 & WPS Encrypted Wi-Fi Access points.
Attackers can attack from different locations and by different techniques.
Audit your own vulnerability and secure your Wii-Fi encrypted network before remote attackers take advantage of the weak IT security to break in.