Scan your websites with the Cloud Penetrator Web Vulnerability Scanner for Cross Site Scripting (XSS) Vulnerabilities easily.
It is important to scan your site for XSS vulnerabilities and eliminate them as soon as possible.
You can also scan for Command Execution and Local file inclusions.
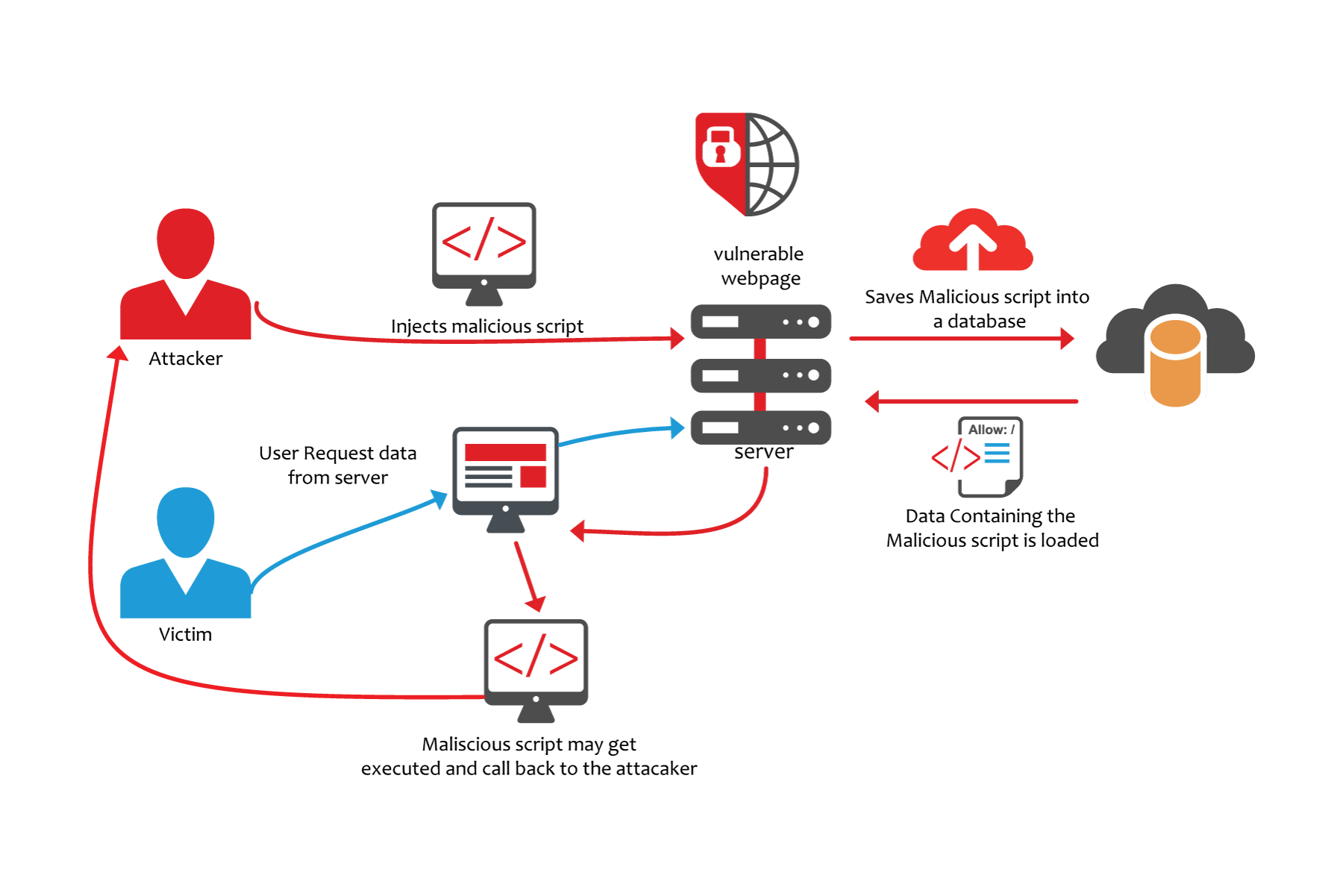
Improperly designed web sites and web applications are receptive to cross site script attacks, whereby scripts are bolted in the domain of the web site rather than just locally on the machine.
Essentially, a cross-site scripting attack consists of a malicious user getting his code to run on someone else´s web page in that person´s browser in the context of the web server.
An end result of cross-site scripting could be a malicious script deleting a user´s account off the server or making purchases for him.
Cross-site scripting attacks allow for cookies to be read or set, and browser plug-ins scripts, native code or even controls can be started and can run unfrosted data.
With this code running, user input such as a credit card number, home address, or other sensitive information can be captured and therefore compromised.
Any browser with a scripting engine can be compromised through this type of attack, and any web server using HTML forms is at risk for being open to this.
One way to check for cross-site scripting vulnerability is to fill out a form with some easily recognizable data (for example, 1111111111 or AAAAAAAA) in all fields.
On saving or manipulating the form, check the form source for this data being stored in hidden fields or other areas.
Appending a parameter to your URL (?cmd=AAAAAAAA or ;AAAAAAAAA), hitting Enter, and then searching the resulting source can also tell you if the parameter is attack.
Other holes are created through assumptions, such as what domain the code is coming from.
In these cases, the URL standards need to be carefully followed, and the IE functions need to be used to determine what domain is being referenced rather than going off and writing your own functions.
The real problem at the heart of any cross-site scripting attack is that the Web page displays data that has not been validated by the server.
This risk is created through poor coding and poor architecture of the application.
Cross-site scripting is most usually a shared data problem because the data is provided by a malicious user.
The typical points of attack are:
Through query strings issued to the database, by way of data posted to the server, through URLs or pieces of URLs cookies, or other user-supplied data that is persisted in some way (usually in the database)
To exploit a server, all that a malicious user needs is for one server inside the firewall to no check a field in a form for special characters.
The same precautions that protect the application and user from other attacks also work here.
Data should be verified as safe before using it, by escaping, filtering input, and filtering the output if necessary.
Again, many of the vulnerabilities can be eliminated with proper escaping of input and particular characters.
If all data is handled properly through verification, escaping and filtering cross-site scripting is generally not a problem.
Tools for testing cross-site scripting are: character viewing and generating tools, network monitoring tools.
Reliable methods to avoid cross-site scripting vulnerabilities needs the encryption of all special characters used while coding HTML in potentially malicious data.
This prevention method is usually applied right before the presentation of a client-side script or the web applications, and several programming languages have libraries or built-in functions which supply this encryption (in this context, also known as escaping or quoting).
One of the problems while dealing with cross site scripting vulnerabilities is that every situation is different.
Each time, the method used to hack the system varies and thus the issues.
For example, in the case of user input, the src attribute of a hyperlink, cgi.escape() would be enough to put things upside down.
There are several ways to fix these issues.
However, one of the drawbacks of this fixing is that users will not be able to embed malicious HTML into pages.
This is because HTML standards do not have scripts to perform such actions.
Security on the web is in light of an assortment of instruments, including a hidden idea of trust known as the same-starting point arrangement.
This basically expresses that if content from one site, (for example, https://mybank.example1.com) is conceded authorization to get to assets on the framework, then any substance from that site will impart these authorizations, while content from another site (https://othersite.example2.com) will must be allowed consents separately.
Scan your site for XSS Cross site scripting for free
Cross Site scripting uses known vulnerabilities in online applications, their servers, or module frameworks on which they depend.
Misusing one of these, aggressors fold pernicious substance into the substance being conveyed from the bargained site.
At the point when the subsequent joined substance touches base at the customer side web program.
Iit has all been conveyed from the trusted source, and subsequently works under the authorizations allowed to that framework.
XSS or cross site scripting is a "popular" type of security hole among "old-school" hackers that's also one of the most common vulnerabilities out there as well.
The most popular websites on the Worldwide Web continue to suffer from this weakness in one form or another, even in light of all the encryption advancements and advanced safety measures being implemented to ensure the security of any given page.
XSS is a favorite among hackers to exploit; it can even be called a "classic" in the realm of IT security problems, which means it is right up there with spam and viruses as the oldest of security flaws around.
That's right, there are XSS flaws in Symantec, PandaSecurity, K7Antivirus, and QuickHeal as well as popular sites like eBay, Adobe, and Amazon.
It's ubiquitous and it's everywhere.
This web app vulnerability enables hackers to deploy their own external VBScript and JavaScript on a web-based program and unleash virtual hell on the poor thing as long as the vulnerability isn't addressed.
A toxic concoction of malicious code galore will easily invade and infect any site with an XSS security hole within its code, such that it's practically a sitting duck as long as that vulnerability remains unpatched and un addressed.
The malware can be executed on any browser to boot.
Hackers have made it a sport to find website XSS, whether they're black hat, white hat, or gray hat hackers.
It's just your luck if a black hat hacker had found your vulnerability and he has set his sights on your exposed site to "teach you a lesson" or to simply entertain himself.
He might even use XSS to take control of your financial accounts if you're incidentally an online banking site or financial institution. Cookie stealing for the sake of causing session hijacking is the most popular application of XSS.
As soon as your browser history and cookies are accessed with full read/write privileges by a hacker, he'll be free to execute his malware on your site with extreme prejudice.
As for hunting down for XSS, you should hope to the high heavens that it's a security team or a white hat hacker who found your XSS first before the black hat.
If a website is coded in such a way that sanitizing or filtering user input properly is beyond the scope of its capabilities, then it's a definite candidate for possible XSS vulnerabilities, since it's usually executed as a kind of user input.
User input in this context can come in the form of profile forms, login forms, search forms, and so forth.