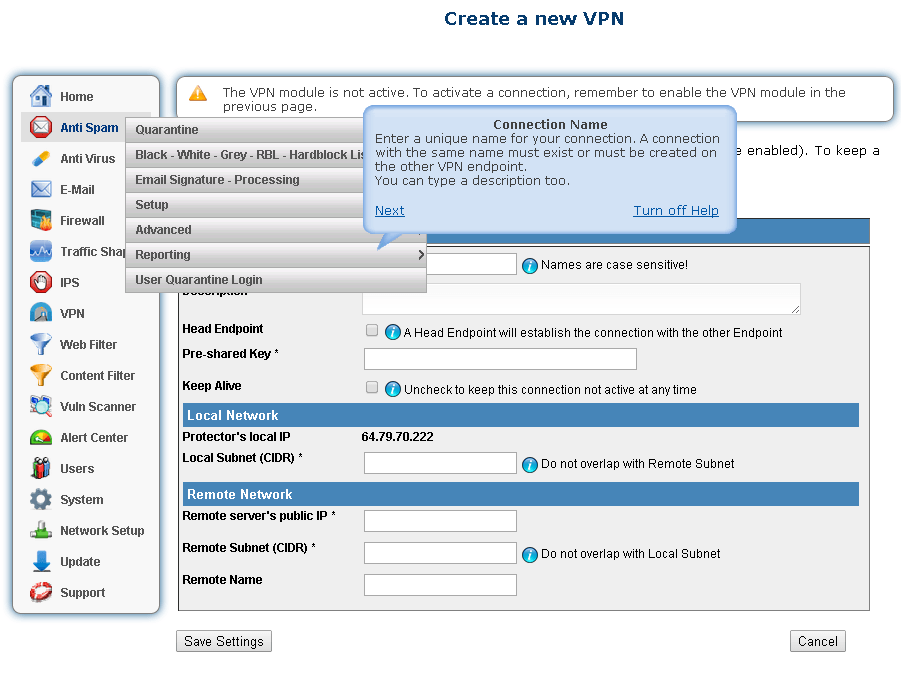
With the Protector UTM VPN Firewall appliance you will get full LAN to LAN vpn support.
Easily setup the LAN to LAN VPN connection.
This can allow to connect 2 departments or locations in a secure way.
VPN, which is the short form of a virtual private network, is basically a private network that is spread across a public network, for example the Internet.
There are a number of different uses of a virtual private network.
For instance, a virtual private network could be used to protect a computer; as information passes through a private tunnel.
It doesn’t become available for website servers, which are able to gather information regarding the end user.
For instance, a person who wishes to maintain his/ her anonymity might use a powerful VPN in order to create a ‘virtual private network’.
That will then ensure that their real location and internet address is not revealed.
By using a VPN, employees of a company are able to access the intranet of the company as they travel outside of the office.
Apart from that, VPNs can also be used to connect offices that are situated on geographical locations to connect in a secure manner with each other, resulting in the creation of one, cohesive network.
Simply put, using a VPN allows for the creation of a smaller scale ‘private network’ based within a larger scale network, such as the Internet.
Then, the data/ information is sent over the virtual private network, and is then decapsulated at the end of the tunnel; where decryption also takes place and then the packet is forwarded to its original destination.
Datagram Transport Layer Security- This is technology that is commonly featured in the Cisco AnyConnect VPN as well as the OpenConnect VPN in order to resolve the issues of the SSL and TLS security with the tunneling of the User Datagram Protocol.
Using a VPN has become a common feature in numerous organizations as well as for individual purpose, which makes it much easier for people to manage their connections on the internet and to ensure that security is provided.