Penetrator Vulnerability Scanner Questions FAQ
Do you have a question about the Penetrator Vulnerability Scanner?
If your question is not featured please mail us or you can always Live Chat us.
Please see the full list of questions in the right side menu.
The questions covers questions of technical, installation, and sales nature.
If you need help to choose the right Penetrator version you can find help as well.
Find more questions in the right side menu.
Which Image size to use in Penetrator Reporting?
The image must be Width: 432 pixels, Height: 131 pixels, or any other pair with the same ratio. The font is automatically reduced when the line to display is too long and won't fit the page width.
SCADA Question
Starting with the easy part, it is a 1 time scan once the deployment has been completed.
QUESTION: does the AI/ML requires a recurring scan over the same network?
In any case, as you have mentioned, it will be interesting for us to have your consultancy services in order to produce a more consistent report.
Thanks for the document provided with the scan profiles outline. However, Profile 10 only mentions SCADA ICS PLC, so I am not sure if this is applicable for our WAN Gateways.
QUESTION: how does this profile apply to IoT networks if it refers only to SCADA?
The demanded solution has are many different components. There are mainly different systems to be deployed under one big project/RFQ: public digital signage points, public WiFi hotspot, BLE beacons, environmental sensors, public web portal ...
All the systems will require an on-premise management software installed in a virtual machine. So we will have management machines with public and local interfaces. I will try to represent it:
-------- ----------------------- ------ ------------ ---------- ------------- ---------- ----------
| | | | | -------- | | | ---------- | | |
| | WiFi Controller | | | | | | | | | ||Layer 2 | |
| <------> Manager <-------------------------------------------------->Access ||(WiFi) <-> Clients |
| | Radius Server | | | | | | | | | Points || | |
| | | | | | | | |Private IP| ---------- | | |
| |-----------------------|Public| | |Mobile | | |(from ------------- ---------- ----------
| LAN | |IP | | |3G/4G | | |carrier) | ---------- | | |
| <-----> Sensors Management <-------------------------------------------------->WAN ||Layer 2 <-> Sensors |
| | | | | | | | | | | Gateways ||(WAN) | |
| | | | | | | | | | ---------- | | |
| |-----------------------| | | -------- | ---------- ------------- ---------- ----------
| | Web portal | | | Internet | | |
| <-----> <-------------------------------------------------------------------------> Clients |
| | | | | | | |
-------- ----------------------- ------ ------------ ----------
We could target servers (LAN and public sides), but we do not know how to proceed with field elements as Access Points and WAN Gateways, as the will be inside the 3G/4G carriers network.
Also, we can conduct some kind of WiFi pentesting (QUESTION: you have a product for WiFi, isn't it?) but we do not have a clue how to pentest WAN Layer 2.
So, let me know how you think we could approach this project. It is not specified that you must pentest "all" the elements in "all" interface, so let us know what it makes sense to propose.
Reply:
QUESTION: does the AI/ML requires a recurring scan over the same network?
Answer: It does not necessarily require a recurring scan, but the precision of false positive detection grows as the number of scans grows too.
A more consistent report can be achieved with a human analyses, and we will be apply to provide you with our consultancy service.
QUESTION: how does this profile apply to IoT networks if it refers only to SCADA?
Answer: This profile is especially designed for SCADA systems, distributed systems for monitoring and supervising physical systems, but is also applicable to IOT, where the monitoring system is built in the physical (monitored) system.
QUESTION: you have a product for WiFi, isn't it?
We have a product for pentesting WiFi networks via the WiFi Pen testing module.
IoT Scanning
Moving out the central servers, these RFQs include the deployment of IoT infrastructure, an WAN (more specifically WAN) network of sensors.
a) Would the Scada/IoT profile apply for this scenario?
b) Do you have some information about this IoT profile we could include in the quotation?
c) Could it be run against the IP side of the WAN gateway? Or it is only applicable for network servers?
d) Would you recommend any solution for a layer 2 WAN pentest?
a: Yes it is a good choice and the best scan as well
b: yes c: Can you give example of setup so we can check
d: I have to check on this maybe if you have diagram of their setup?
OWASP TOP 10 Question
Regarding a generic pentest for servers and central software,
a) would you recommend the "OWASP Top 10" profile?
b) Does the "Full scan" includes this OWASP profile and also add extra tests?
c) In other words, are there significant differences between OWASP and a full scan?
a: Yes it is good profile or just use the Best Scan it can check for more things
b: Yes same as best scan. The difference is it do 65k ports where best scan do the 2-3000 most popular ports
c: Full scan will scan for more things so it is recommended or best scan
Just want to ask is there an options in the Secpoint that you can exclude some services or port?
Yeah
It is very easy
When you do a scan you click advanced setup
and then you just add the port you want to scan example 443, 80
then it ONLY scan 443 and 80
What is a format string vulnerability
Most common command in C is printf. Example when loading a value such as int value %d.
How can something that just prints text be exploited.
Example char *string so example printing %x %x %x %x this can be used when reversing C
printf can read whatever it find on the stack memory leak vulnerability. You can leak all sorts of memory from the stack.
It can leak stack addresses which can be used in buffer overflows.
Bugs like heartbeat was leak of memory. If something comes from %n writes amount of charters in a variable. Whatever value on the stack can be used for printf to print.
Using %x to %n can allow for code execution.
What is GPU Password Recovery Word Lists , as per below screenshot
It means large wordlists they are also included in Penetrator interface but some prefer to download wordlists as standalone files.
Can we setup SecPoint on AWS/Azure or private cloud, if yes then explain how.
If no then what could be the possible reason or challenge. The Penetrator Images are available in VMware Player, VMware ESXi, MS Hyper-V, Linux G4l. You can easy convert to other forms from those Images.
What are the System requirements, is it as per the IP Slabs?
The Penetrator is optimized for high performance. So you can run on low spec i5, 4 gb ram and increase specs for higher scanning.
Which ports needs to be enabled if doing VAPT remotely, from my office to customers office in other location?
No specific ports required to be open.
If you do Node scanning with the Penetrator some ports can be required to open this will be shown in the interface.
Does SecPoint supports IOT devices, like Smart TV's, Smart home appliances, etc.?
Yes, Via best scan profile, full scan profile, SCADA Iot Profiles.
While scanning Local IP's, what if system restarted?
Penetrator will restart scans if restarted.
While scanning website vulnerabilities, what if system restarted, Will the scanning interrupted?
If Penetrator is restarted it will restart scans, If target system is scanning is restarted Penetrator scan will just continue when the system responds again. If the target takes too long to restart or respond Penetrator scan might time out.
While scanning website, what if VM internet gets disconnected, Will the scanning interrupted?
Scan will timeout you can just rescan then. If you Pause the VM and you resume it later then it will continue from where it was paused.
How to do Node Scanning on the Penetrator?
With Node scanning the IP license is coming from the Main unit only.
So as an example Customer buy a 16 IP Penetrator Virtual Software.
And he install 4 Nodes.
Then it allows him to scan local net from the all the 4 nodes but maximum 16 IPs in total concurrently.
So if he scans
20 IPs on the main unit
20 IPs on each of the 4 Units it will 100 Scans it queue in total.
It will still process 16 at a time.
So they can install all the nodes they want using the main unit license on each node.
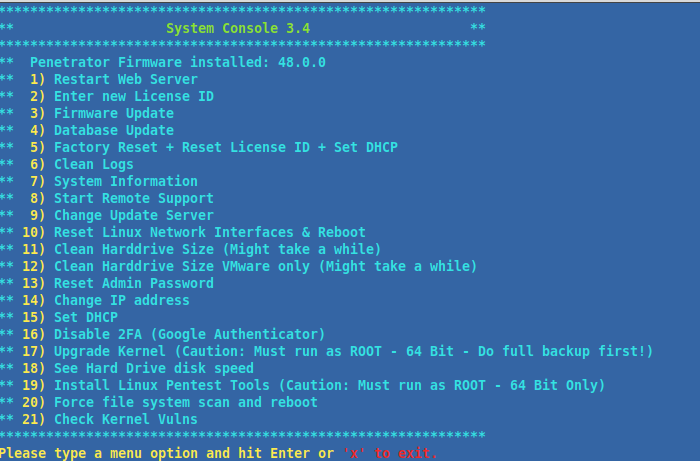
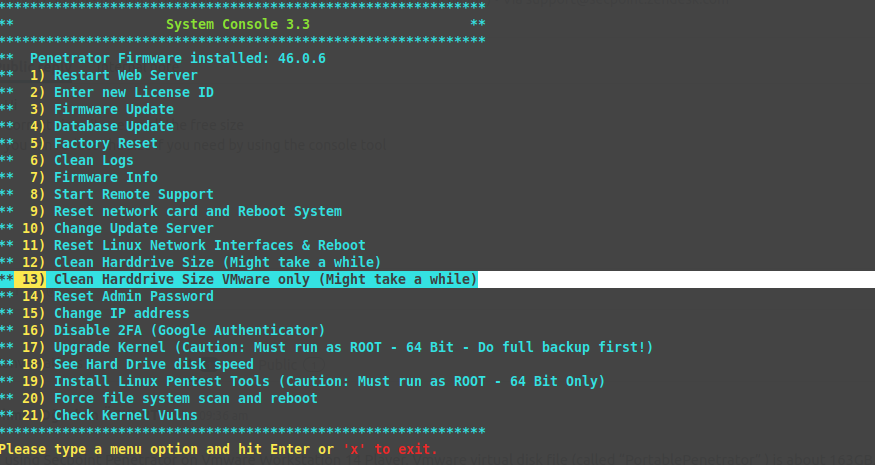
How can I change Penetrator IP Address from console?
From console menu
Menu point 14-15
I want ask does OWASP do harmful attack to the target?
No harmful done in OWASP profile.
Harmful is if only enable DoS and Exploits checks for any profile or use the Aggressive profile which
have those 2 checks enabled by default.
Every other profile have by default disabled DoS and Aggressive checks.
Once the checks are enabled there will also come a red warning.
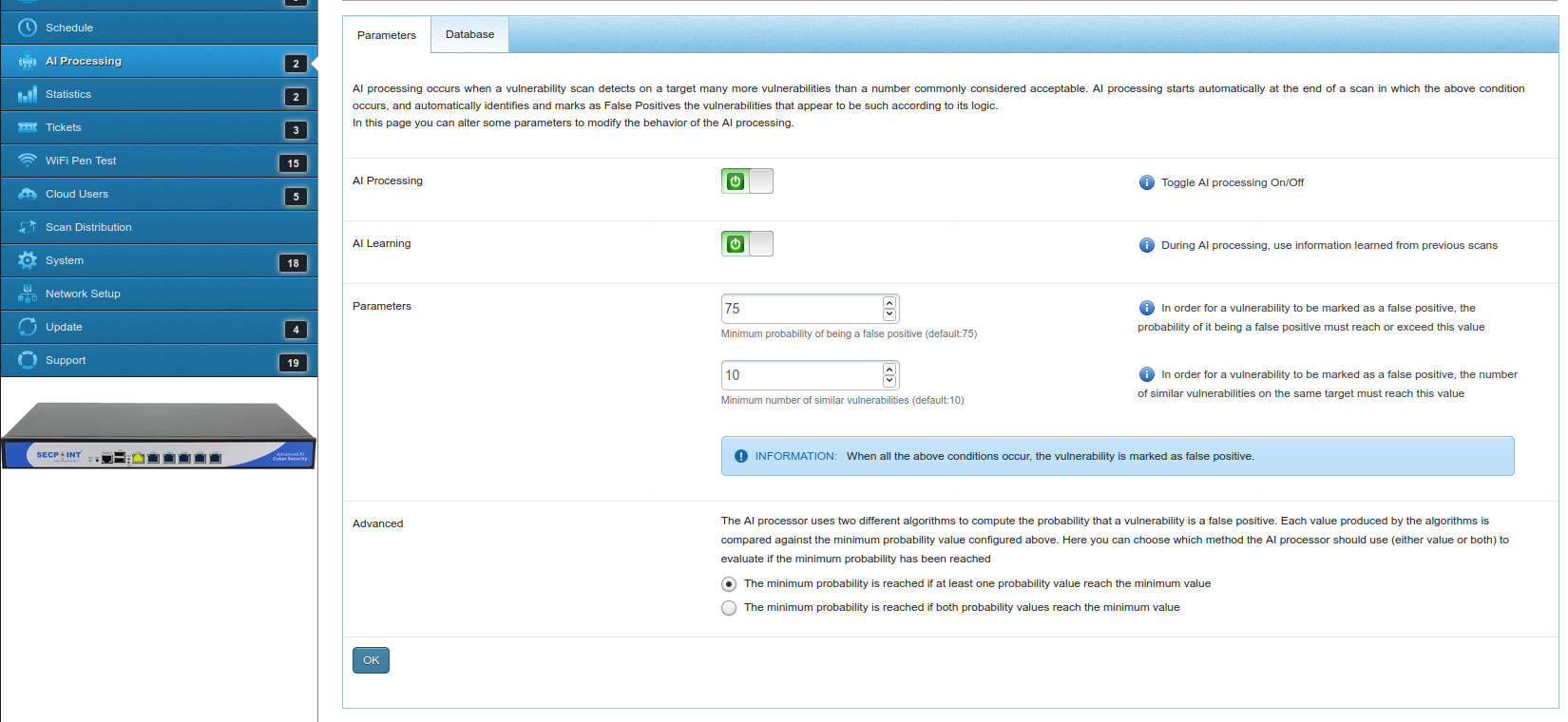
How to control the AI on the Penetrator?
If AI processing is off, learning is not performed, because learning is done "during AI processing", as it says in the Info on the right.
If AI processing is on and Learning is off, every new processing is done as if it was the first time
How to get mail notification when a scan has finished
When doing a new scan in advanced setup you can put in the email address:
and in system smart host relay you can configure outgoing mail sending
How does it compare to free version?
Benefits compared with free version.
1: No or very limited support.
2: No easy update process, in the Penetrator you can just press 1 button to update firmware no reboot even required.
3: Constant new features coming to the Penetrator. It is now 44.1.9 and soon coming v46.
In the free version it can be very limited when new features are coming since there is no paid incentive.
4: New feature request from customer requests being implemented in the Penetrator.
5: You do not know with the free version if it collect data or live up to regulations such as GDPR maybe free tool collect info for people behind it that use it.
VMware player v15 does not connect to internet
Ok can you set Bridged mode.
Then after login to the software and click the network menu
Then select DHCP and click OK.
This way it will get on DHCP to get a new IP address.
See if it got online that way?
Penetrator License Question
For the full edition vulnerability scanning kit it shows IP license. what is the license for the scanner, or the network to scan?
If use by a consultant, would i be able to scan multiple networks, one at at time, or only the one network. unless i have a higher IP license?
It means only concurrent scans.
So if you have a 1 IP license you can still scan 256 IPs it will just do 1 at a time and queue the rest.
When it finish 1 it will do the next.
If you have a 8 IP license it will do 8 at a time.
You are allowed to change the IP and do all the scans you like.
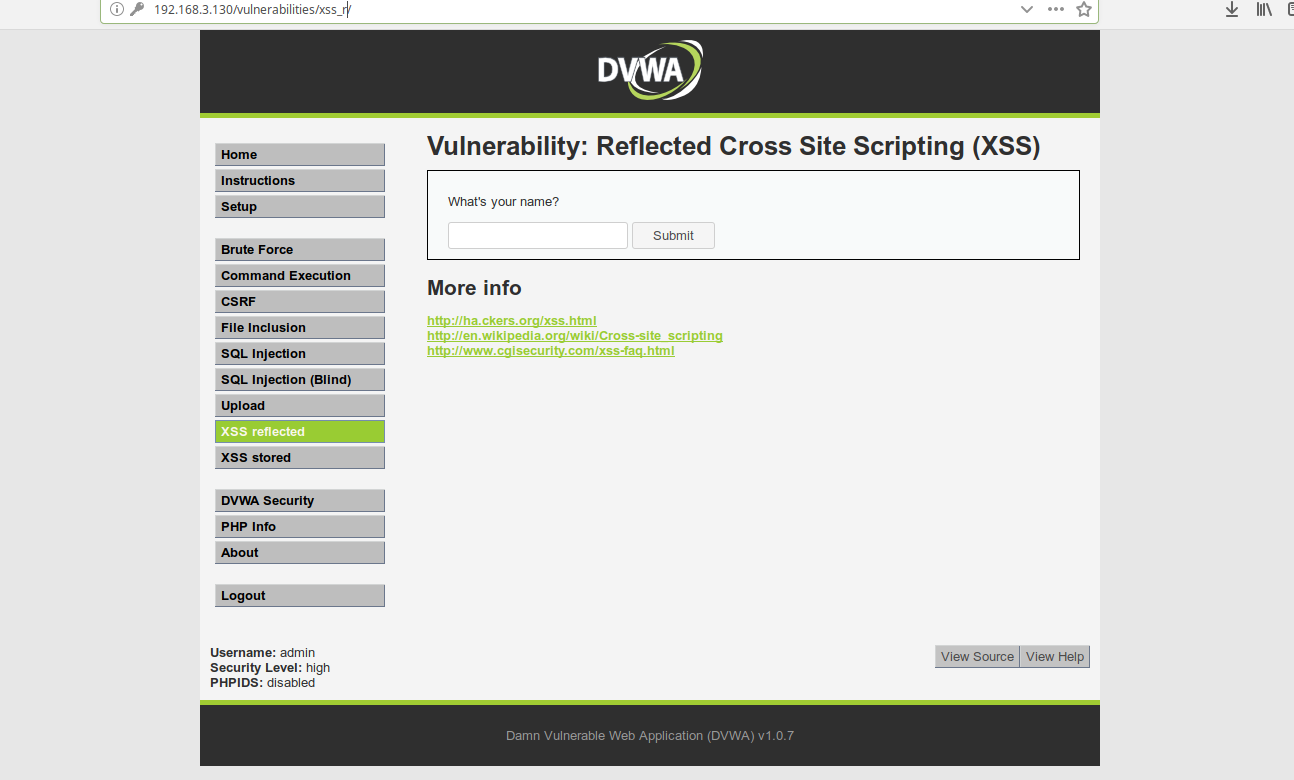
How can I scan a vulnerable web test environment?
You can load up
Damn Vulnerable Web Application
Penetrator Report Languages
Which Report Languages are supported on The Penetrator? Danish Dutch Greek English Spanish Croatian Italian Korean Dutch Norwegian Portuguese Russian Turkish Thai
How many report languages can be set on the Penetrator?
More will keep getting added in new firmware updates
Danish
Dutch
Greek
English
Spanish
Croatian
Italian
Korean
Dutch
Norwegian
Portuguese
Russian
Turkish
Thai
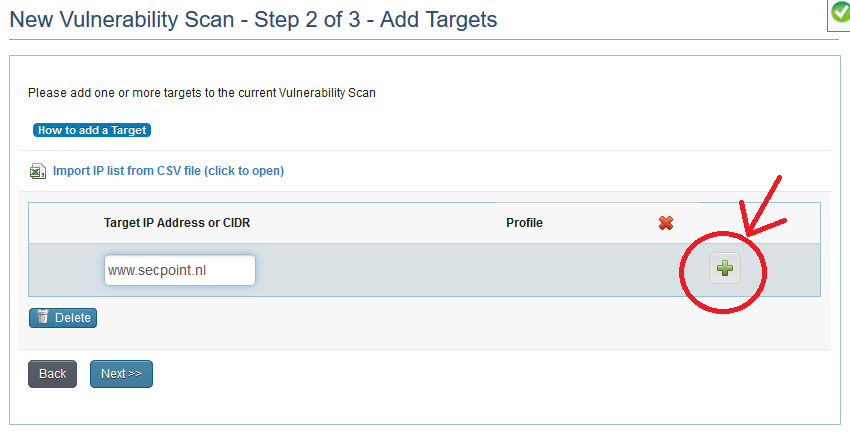
How to start a new vulnerability scan - How to make a scan?
That is just the entry field. They must press Add (the button with the green )
How can i reduce disk size of Virtual Penetrator?
You can reduce the size if you need by using the console tool
Penetrator Offline update?
I have a technical questions about "offline update" without directly connecting to Internet,
Is possible?
Only update via connect to internet, but you dont have to be online to operate the Penetrator
So you can put it on laptop
Go on the Internet 1 time week to update and then just use it for offline mode in other time.
How much faster can quick scan be compared to normal scan?
An example group can be like in this screenshot.
This is an example with 5 IPs in each group scan.
Normal group scan took 07:27:48 (7 hours, 27 minutes, 48 seconds)
Quick group scan took 03:56:21 (3 hours, 56 minutes, 21 seconds)
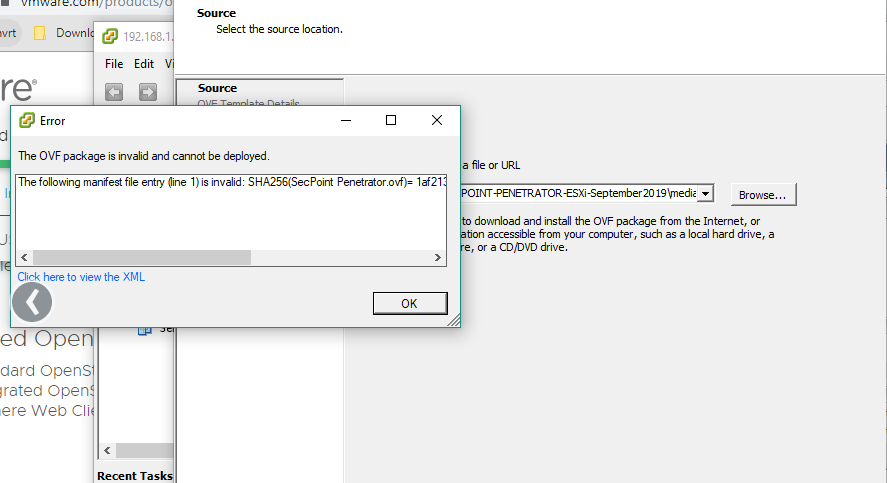
Error importing OVF
We get the errors
OVF Package Error following manifest file entry is invalid. SHA256
We have successfully fixed the issue regarding the lower version of ovf 5.5 esxi no longer supports SHA256 hence we downgrade to SHA1 which helped ovf function properly.
Penetrator Cant Update
We have an issue with our Secpoint Penetrator virtual machine.
We don’t know when the issue occurred exactly
I looks like the networking is kind a broken or something.
Within the web interface the right IP address is configured. We can connect to the internal IP address of the Penetrator website, but the machine cannot connect to the internet.
In the console of the VM, the network icon shows a red cross.
What can be wrong?
I can ping the IP from another PC successfully.
Solution:
You can close the ticket.
I found some strange stuff in our corporate firewall that blocked the connections.
Penetrator Resolution
Resolution problem that the resolution makes the browser to small and menu not shown.
It can be caused by the size of the browser window is too narrow. Put it at full screen to solve the issue or login directly to the IP address from a secondary machine
Penetrator AI Machine Learning
Do the Penetrator support Advanced AI and Machine Learning?
The Penetratort uses Advanced AI and ML in different areas including:
False positive vulnerability scan system to prevent high percentage of false positives to be found.
System Status where it can predict and prevent based on data future system problems.
Can Penetrator work behind a proxy?
On Protector: No proxy support because Protector send mail or make web filtering, and even act as a network bridge which is not possible under a proxy.
On Penetrator: vulnerability assessment can not be done behind a proxy that lets only filter 1 or 2 port.
Which tool must I use to put the G4L image on a usb drive?
You download Ghost4Linux and put it on a bootable USB flash drive with
https://sourceforge.net/projects/win32diskimager/
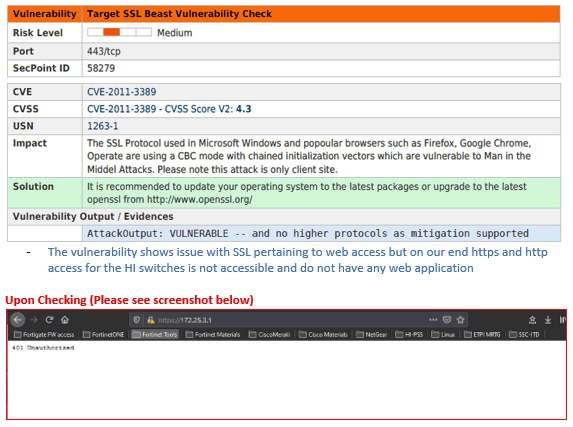
Vulnerability "DNS Localhost 127.0.0.1
We would like to understand how do you come to the vulnerability "DNS Localhost 127.0.0.1 Vulnerability" for scanning specific IPs? Example:
Does it mean that our provider has the vulnerability or resolving localhost. to 127.0.0.1? Which DNS resolver reports this ? I checked a few and some of the resolve it and some not.
The error doesn't point to the scanned ip but to the provider, right?
Yes it must not resolve to 127.0.0.1 it can be used in some attacks.
here example resolve to IP
host localhost.secpoint.com
localhost.secpoint.com has address 207.182.143.131
Penetrator Scanning Profile
Suggestion regarding when and what profile scanning we need to choose
When scanning a Server/Desktop and URL.
Because BEST SCAN has all the scanning either for Server/Desktop or URL.
Reply:
You need best scan profile for things not specified in the other profiles.
So in the case of Server/Desktop then it best the best scan profile.
How can I exclude IP addresses when scanning a C Class?
First, add the cidr. Then add the single IP. It will recognize that the IP is included in the CIDR and will mark it as excluded
Can the Penetrator discover the memcached vulnerability?
Yes.
You can simple run a normal scan or specify only to scan TCP & UDP port 11211.
My IP Address has been blocked from login on the Penetrator
The IP is banned if:
- there are no valid logins from the same IP AND
- there are at least 5 wrong login attempts from the same IP AND
- the most recent login attempt is less than 5 days ago
So, when this happens it's necessary to wait 5 days to be able to login again. The console (127.0.0.1) is not subject to this check.
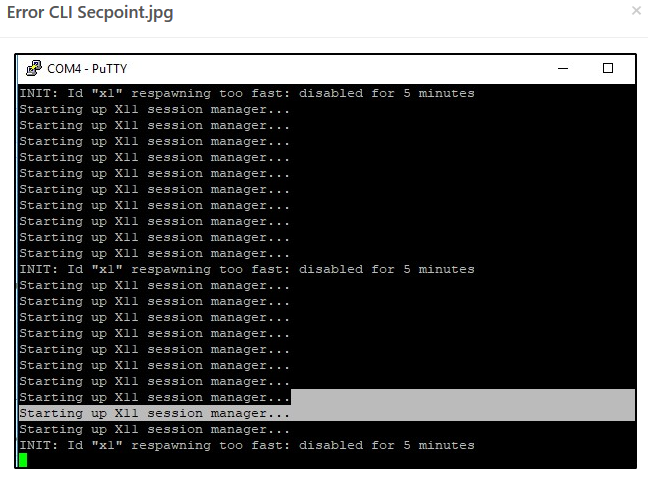
When i try login for putty to the appliance this show me the attached image
Please press ALT F6 or Please press ALT F7
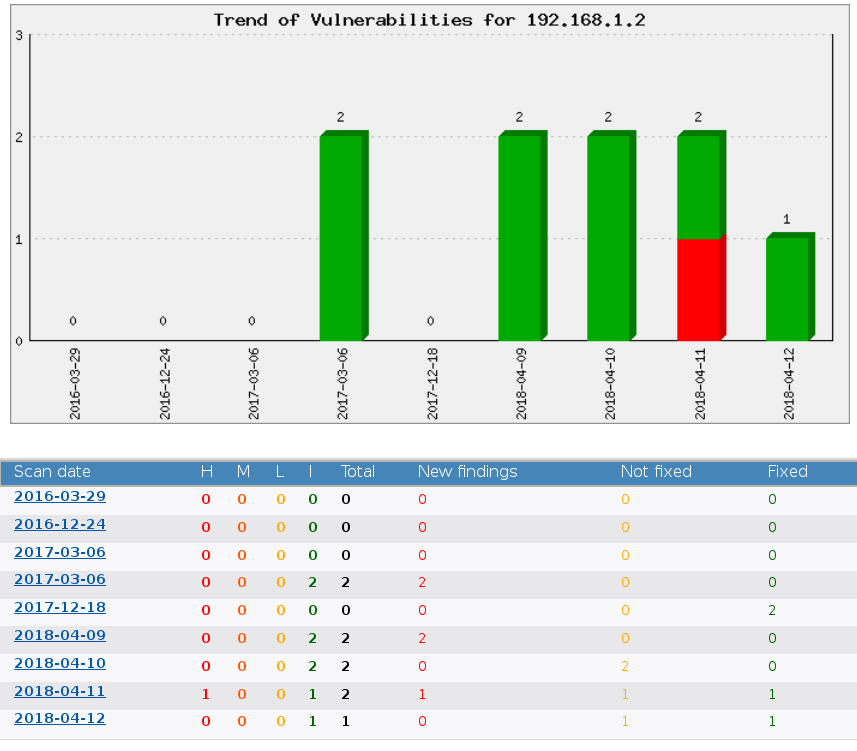
How to easily see IP address history of vulnerabilities?
You only need to select 1 IP, then it will show you up to the most recent 36 scans. Then you can click on one of the scans and it will give you the status of each vulnerability.
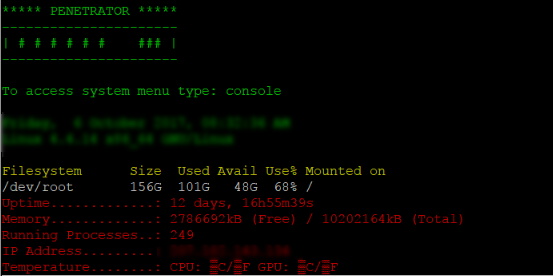
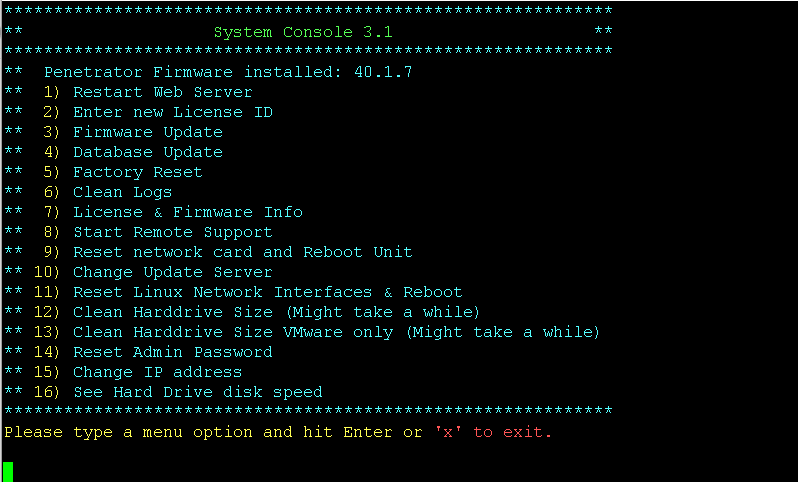
How can I access the system console in the Penetrator?
Type console to get the menu.
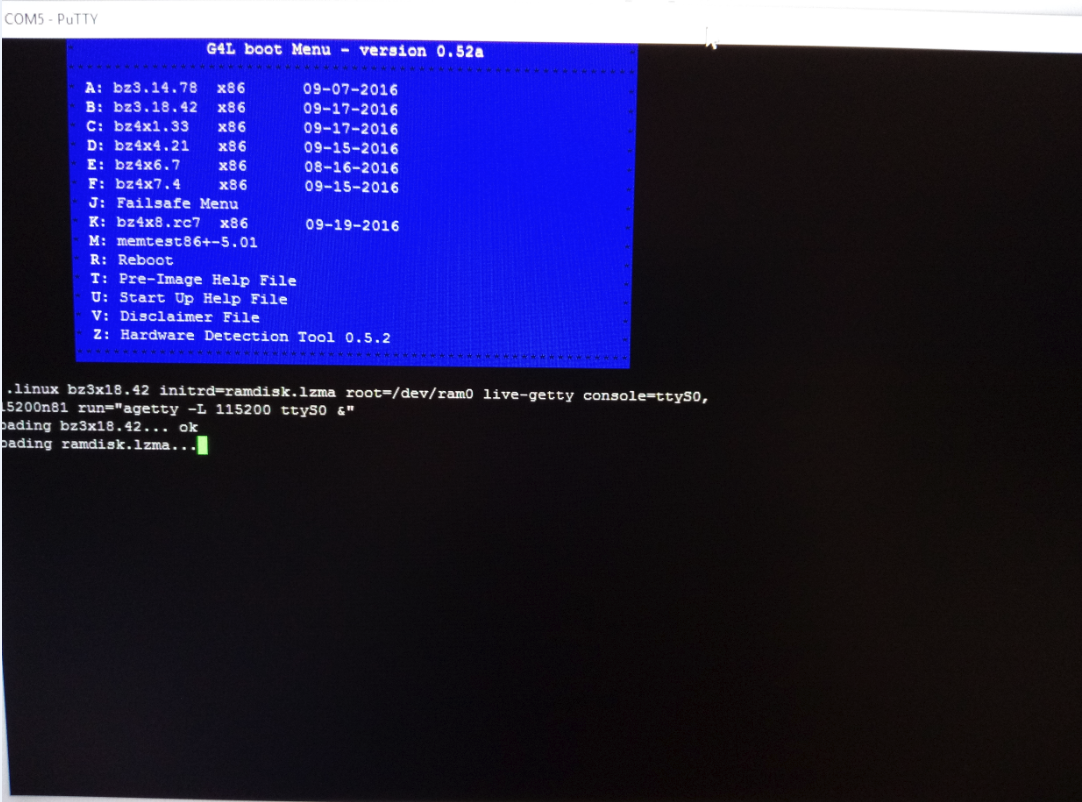
G4L boots up I can type but nothing happens
Booting g4l i can type but nothing happens.
Solution:
1: ok boot g4l
2: press tab at boot menu so you can type parameters
3: Make sure it has: live-getty console=ttyS0,115200n81 run="agetty -L 115200 ttyS0 &"
Internet question when scanning
One of the questions I asked was if this program needed the internet or not in order to use it. I'm just starting out with the software, but its looking like the internet is needed to use this program
It is not required to have Internet to run the program.
How does the Penetrator store data?
Does all the vulnerability scan logs are save locally on the Penetrator device? How large it consumes HDD space?
Correct everything is stored locally and you can also export all scan data In Vulnerability Menu > Download Reports
You can see free HDD space in System > System Logs
How much data will a scan consume?
What is the process name on the target machine while the scanning is on progress? Some end user may ask about it. Or how much resources it consumes during a scan process.
It is designed to consume minimal amount of resources when doing a scan.
It will only sent necessary data based on services detected.
Vulnerability scan improvements
Domain Names visible on screen and reports The Penetrator allows to enter a domain name instead of an IP address when creating a scan. Starting with this firmware the domain names are visible throughout the whole scan process. This feature has been created for scans, scan templates, on scans created from a template and on the Scan Distribution page. The domain name will also be visible on the reports.
Detection of IP addresses
When a scan is created through a domain name, the corresponding IP address is automatically detected at the moment of the scan. When the scan is created from a template, schedule or repeated from a previous scan, the IP address is now detected immediately before launching the scan, not when the template or schedule are created. This behavior allows to detect the correct target from the corresponding hostname when the target’s IP address is assigned through a DHCP server, and is subject to change over time.
Repeated Scans
Two new features are available on the Repeated scans. It is possible to alter the scan parameters, for example when it’s necessary to alter the scan profile or the port numbers of a previous scan leaving all the other parameters unchanged. The second feature is the possibility to repeat a previous scan on the nodes that were offline on the previous scan. To do this, click on the red button Repeat Scan on the scan row.
Operating System Name
Operating System Name
The operating system of the target node is now displayed on the report. The operating system is detected through a set of algorithms, and may not always be 100% accurate. The operating system is shown in a separate chapter of the report.
Google Authenticator 2FA Penetrator
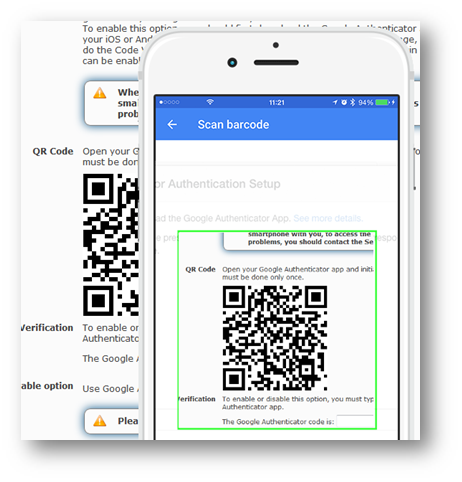
The Google Authenticator is an implementation of the Two Factor Authentication (2FA). 2FA is a means of making account logins more secure. In addition to username and password, it requires a Time-based One-time code that can only be generated by the legitimate owner by means of a hardware device.
This feature is available through menu System > 2FA Login Protection To enable this option, you should first download the Google Authenticator app on your iOS or Android smartphone. When the app is installed, you should initialize it by scanning the QR code displayed in the 2FA Login Protection page. After that, the Google Authenticator app will start generating numbers.
When the app is installed, you should initialize it by scanning the QR code displayed in the 2FA Login Protection page. After that, the Google Authenticator app will start generating numbers.
|
The QR code is unique to your Penetrator, therefore you can only use it to login to your Penetrator unit.
|
|
This step is necessary to enable the 2FA, since it cannot be enabled if the code generator is not in your hands or hasn’t been correctly initialized.
|
To proceed, you need to do the Code Verification: type the
number displayed on your smartphone in the entry field on this page. If you see the green check mark next to the code, it means that the code has been accepted. If the Code Verification is unsuccessful or hasn’t been performed, the Google Authenticator option remains disabled and a warning message will invite you to complete it. At the end, the Google Authenticator login option can be enabled. When you want to disable the Google Authentication, you need to do the Code Verification as well. When the option is enabled, the Penetrator login page requires an additional field, the Google Authenticator Code, that can be read on your smartphone. If you omit this code or if the code incorrect, the login is denied.
When this option is enabled, to access the SecPoint® Penetrator you will always need to have your smartphone with you. In case of access problems, you should contact the SecPoint® Support.
New User Interface Penetrator
Starting with this firmware, a new User Interface is gradually replacing the previous one. Along with this, most of the existing functions are subject to rewriting, to comply with the new interface and for more robustness. Here are the main features of the new interface: New layout with different colors: Top banner, tables menu and widgets in different shades of gray Responsive design, for a better experience on classic and touchscreen devices A larger window is available for displaying data New left-side menu, usable on touchscreen devices New User menu on the top banner
New widget for on-off switches Collapsible right-side panel with overall status always visible on the page. The available states are OK, Information, Warning, Error. Ø Flashing icons to emphasize issues Ø Data tables with paging, filtering and sorting Multiple selection and actions on multiple items at once
abs to display multiple pages at once The new user interface is currently available on the following menu items:- Vulnerability Scanner > Download Reports- Cloud Users > User Management- Scan Distribution
User has no scans left
I am trying to run a new vulnerability scan with our device but it says "You can't make any more scans."
I'm logged in as admin
under "User Statistics" it says: Total scans left 0
any idea how to fix this?
Solution:
If you see the picture, the user has zero scans left. You can change this restriction in the user management, parameter Scan limit.
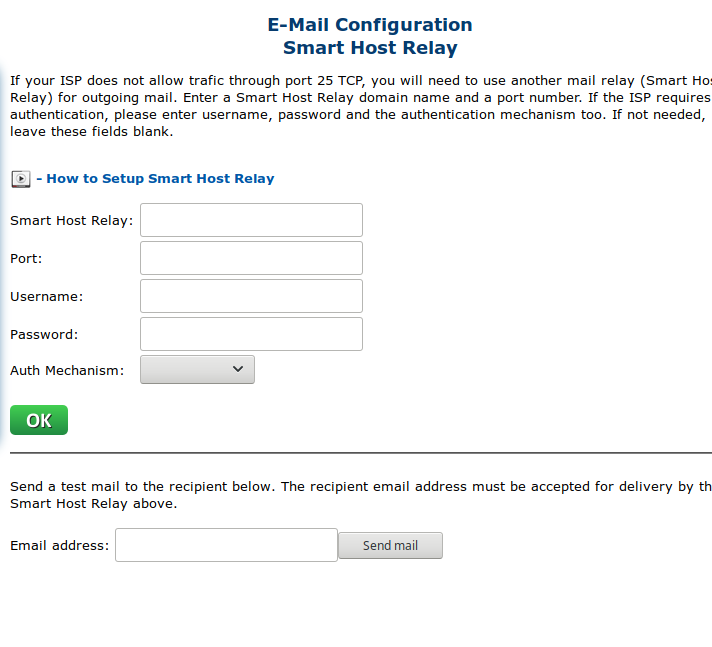
Penetrator cant sent mails
My Penetrator cant sent mails.
You need to put in your ISP relay server.
This can be done here
System > Smart Host Relay
Question about Penetrator Distribution License
A customer has a very interesting question
1) Let say I got a Penetrator with a 1 IP license online in a Cloud VM
2) I got a SFF Penetrator appliance 8 IP in a remote network behind a NAT router
3) Let say I got the master/slave Penetrator working ( we still got it NOT working)
4) When I create a scan on the “cloud” penetrator to the slave Penetrator Can I start a scan of 8 devices on remote SFF from the Master 1 IP cloud Penetrator?
Reply:
The license type creates a funnel that defines the way the Penetrator starts scans. In the case of a master-slave architecture, the two funnels do not combine, so that the master and the client Penetrators will launch scans depending on their own license only. In your case, the client Penetrator will receive the command to launch the scan of one or more IPs even if the master is already processing another IP. So, you may create a scan of 9 IPs and let the master process one and the client the remaining 8, that would be launched simultaneously.
If the master-client is not working, please upgrade to the latest firmware on both units and retry. If it shouldn't still work, please open the remote support.
Penetrator Performance Impact
May we know if their is an performance impact to the device if secpoint penetrator is in the process of scanning the vulnerabilities on that device?
It is designed to cause minimal impact and not interrupt with production systems.
So even if you scan a production enviornment during business hours the customers should not see any difference.
Often with poorly written opensource tools if using during production hours can end in target systems to crash.
We have designed our tools to not crash the target system or lower performance.
You can via the more agressive scan profiles still perform DoS and exploits
If their is no impact, what scanning technologies that secpoint do to avoid performance issue during scanning?
It is good written code that takes into account not to crash things.
Only if you choose the agressive profile it will try and crash the target system.
It is also designed to not sent data if it has not detected a service.
So it keeps minimize the data footprint on the network in each scan.
50 IPs for Penetrator?
For SecPoint Penetrator number of IP’s, I will be preparing quotation for 50 IPs for 1URack, but in provided pricelist there is no exact number for 50 IPs ?
It goes in format as 8,16,32,64 etc.
So in the case they need the 64 IP 1U rack.
What is the difference between Portable Penetrator full edition and Penetrator S9
Portable Penetrator Full Edition and Penetrator S8 is the same.
The only difference is that Portable Penetrator comes in a Light version that is WiFi Pen Testing only.
How about the new profile scanning the SCADA?
How it works and what is it main purpose?
SCADA is typically industry or hardware control systems.
It can be Traffic light, Swimming pool system to regulate chlorine in the water, Factory machine, Heating system.
All systems if being hacked or compromised can cause harm.
So if they hack a swimming pool and increase chlorine it can kill or make people sick in there if they don't find out.
Or if it is machine factory where they disable cooling system so it can break.
All industry systems have very poor security because it is not designed to be accessible by hackers only by factory workers or engineers.
So with the SCADA module we can scan large amount of SCADA systems different vendors such as:
SCADA (Supervisory Control and Data Acquisition)
ICS (Industrial Control Systems)
PLC (Programmable Login Controllers)
Niagara / Foxboro / Moxza / Emerson
GE General Electrics / Hitachi
Mitsubishi / Panasonic / Rockwell
Fisher / IEEE / Schneider / Beckhoff
OSIsoft / OMRON / OPC / ABB
Iconic / SNC / Sielco / Telvent
RUGGEDCOM / Danfoss / Modbus
Phoenix / Siemens / Tridium
Our scans seems to get stuck after 1 day
The last scan was running 4 days.
We ran a couple of test scans but they stop progressing after 1 day.
Follow up:
We did a scan on a diffrent website hosting.
I checked in our fortigate hardware and the secpoint ip was being blocked several times.
I made an exclusion for it and am running the scan again.
The fortigate was indeed the problem.
Scans are now completing.
Schedule options on Penetrator
A new feature in the schedule options allows to plan the launch of a vulnerability scan with more accuracy. Through this option it’s possible to specify the date and time when a scan must be launched and optionally the number of days to wait before the scan should be launched again.
Schedule scans are available through menu Schedule.
When you are creating or modifying a schedule, the list of frequencies contains the new option “On Date”, where you can enter the date and time when the scan will first be launched.
If the scan should be repeated, enter the number of days between the first scan and the next one in the entry field on column Repeated. In this example, the scan will be first launched on Friday, August 10th 2018 and repeated every 2 weeks, on Fridays, at the same time: August 24nd, September 7th etc.
With option “On Date” it’s also possible to launch a scan later in the same day.
Please take into account that a 1-time schedule scan will not be deleted when the scan has been completed, and it will remain in the list of scheduled scans even if won’t be launched again.
In this picture scan “Old schedule” has been performed on January 1st 2018 and will not be repeated. If no more necessary, a schedule can be deleted. If you need to schedule it again in the future, you can edit the schedule and change the start date/time.
2FA Recovery Code Penetrator
In order to avoid any valid user to remain locked out of the door of the Penetrator when the code generator is unavailable, a Recovery Code is now available.
This code is displayed on screen in the 2FA page (Menu System > 2FA Login Protection) and is only visible when the 2FA feature is enabled.
This code must be copied and stored in a safe place and only used in case of emergency to disable the 2FA feature.
The 2FA feature can be disabled by logging in to the Penetrator’s command line, and opening the Recovery Console. Here, option 16 will ask to type the recovery code and, if the code is valid, will disable the 2FA feature. The recovery code is unique to each Penetrator, therefore it can only be used to unlock the unit where it was generate
CVSS Scoring System
When a vulnerability found on a specific target can be referred to a code in the CVE database operated by the Mitre Corporation, the Penetrator will automatically find the corresponding CVSS score for both V2 and V3 versions of CVSS.
The CVSS score will then be displayed on screen and on the reports whenever a CVE code is available.
The CVSS score is available on screen in the detail of vulnerabilities: when you click on a snapshot icon , the list of the vulnerabilities for a scan is displayed.
Here, clicking on the name of a vulnerability, the Penetrator shows the page with the details:
The same information is also available on the reports.
Please take into account that the reports available on the home page have been created at the end of each scan. Therefore, to get the CVSS score, it’s necessary to generate new report: click on Make New Reports in the floating menu in column Options next to each scan.
The CVSS scores are updated frequently, and the Penetrator keeps its database up to date accordingly. The Penetrator automatically updates the CVSS scores every night between Midnight and 1 AM. This process is necessary and may require some time if it’s not performed frequently.
Just want to clarify how does the Secpoint Penetrator able to detect a malware on the system?
What is the approach and what engine it uses to detect malwares?
Yes if it comes in via the Network.
The customer still need a malware scanner on the PC to protect from USB disks.
What is the approach and what engine it uses to detect malwares?
Only if they open services/ports.
Penetrator scan over network
If something on hdd you need antivirus to scan locally.
But most antivirus is not effective.
So you need use our Protector UTM Firewall with Intrusion Prevention module to block malware before it even gets to the hdd.
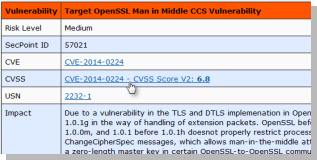
Penetrator Report can show CVSS?
Yes after firmware version 43.0.3 or newer.
Authenticated scans
There can be a risk with authenticated for any data loss..
The customer must be aware if he use this function and it login to an interface while query for sql injection, command execution, xss etc there is a big risk of data loss.
If using it then he must have backup 100% of everything or testing offline a system.
How can I access the serial port on Linux?
Please use putty or simple use:
screen /dev/ttyUSB0 115200
Is there a demo online?
Yes please fill out the Free Vulnerability Scan here.
Does it impact the network much when scans are run?
No it is specially designed not to impact the network while scanning.
The Penetrator has 9 profiles to choose from.
From very safe to more aggressive to use on pre production servers.
What is the cost?
What is the cost breakdown for IP's?
Please see our Webstore or contact Sales for a local Reseller.
Is the software updated regularly?
Where do the scan come from?
How does the software act like it is coming from outside our network?