The SecPoint Penetrator vulnerability scanning software engine is designed to have the best, most intelligent & most effective scanning capability based on the presented scanning methodology in this document.
Using the same approach, techniques while scanning as real attackers/hackers & black hat hackers would deploy to compromise a target system or systems.
The vulnerability scanning software engine don’t just rely on attacker’s black hat approach it is also optimized for government & corporate environments to give the customer the most optimal scanning process.
Utilizing scanning feedback & requirements from thousands of customers across more than 100 countries allows the Penetrator software to get a better result than traditional scanning solutions.
The preferred steps for successful network attacks.
Phase 1: Reconnaissance - Obtaining the biggest amount of sensitive information about the target systems as possible.
Phase 2: Vulnerability Scanning - Discover all vulnerabilities on the target systems that can lead to full system compromise, remote command execution.
Phase 3: Gaining Access - Via different ways gain access into the works to show the clear goals of getting in.
Phase 4: Maintaining Access - Have full access to the network to accomplish attacks and goals that are set.
Phase 5: Covering Tracks - Like a real attacker that can hide the attacker presense on a network so it can not be traced in any way.
The SecPoint Penetrator Vulnerability Scanner & Assessment product methodology is build up in the same way as a real attacker would target a system.
It uses advanced techniques for information discovery juts like an attacker would do it.
The Penetrator Scanning engine is updated with the latest advanced scanning modules to comply with the scanning tasks.
Optimized with an intelligent scanning backbone structure to maximize overall performance, data traffic, scan speed & scan results.
Taking advantage of detected services for faster results.
The scanning engine modules can utilize threads for faster but accurate scans results.
This can increase overall performance when scanning large network segments.
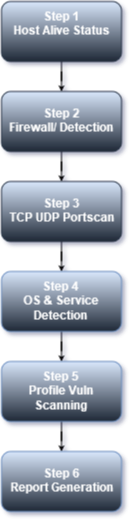
Checking if the target system is alive & information gathering.
To consume data, use the most optimized scanning the Penetrator will determine if the target IP address must be scanned.
It uses different techniques for this to also detect firewalled systems or otherwise hard to detect a pulse from.
One technique is to probe for open TCP & UDP ports.
Popular ports includes but not limited to TCP Ports 1-111,135,139,443,445 & more.
For UDP 53,111,135,137,161 & 500. It is also possible to customize the profile to add other ports.
A scan can also be forced even if the target appear to be offline or not alive.
Determine if the target system is behind a firewall, IDS or IPS system.
Some systems appear to be offline where in reality they are just firewalled off & can still be wide open to attack.
In the Firewall detection module it can use different techniques to detect firewalling/filtering/IPSed devices.
The test will also gather more network information from the infrastructure when doing TCP & UDP port probing.
TCP & UDP port scanning to determine open ports & services.
Depending on the chosen profile there can be scanned the most common 2000 ports or more.
In the full profiles all 65.535 TCP & UDP ports will be probed & scanned.
In most setups using the best scan profile can be recommended to save time & network bandwidth.
For more in-depth analysis the full scan profiles are recommended.
Services, OS & services version detection. Operating system detection & optimizing.
Once the TCP & UDP port scanning has completed, the Penetrator will use different techniques to identify operating system running on the target host.
Based on selection of one of the nine scanning profiles selected.
Right profile is applied for optimized Vulnerability Scanning results.
Launch scanning modules, exploits or Denial of Service (DoS) depending on which of 9 profile selected.
Reporting Generation in different formats and outputs risk analysis and remediation suggestion.
Scanning software programs come in a large variety of different kinds.
There are scanning software programs designed for use with your computer, which can be used to detect any sort of anomaly that might exist within.
Apart from that, however, there are scanning software programs which are used in networking as well.
For networking the number of tasks performed by scanning software programs usually tend to vary.
In the following article, you will learn more about scanning software programs as well as their usage in different fields of computing.
The main job of scanning software when installed in a computer is to make sure that the computer itself is working properly.
The scanning software is able to scan through the whole computer and find out if there are any sort of errors or any malicious programs running within.
Files that contain viruses, worms or trojans are all harmful to the overall health of your computer, and can cause a sincere amount of damage.
As a result, the scanning software will scan through the hard drives, as well as the registry in order to detect any sort of malicious activity.
If it does find any sort of harmful activity, the software program will automatically inform you.
Most of the top scanning software programs that are available today also come fitted with the latest antivirus capabilities, which allow them to put the files in quarantine, or permanently delete them from your computer.
Managing a network is of vital importance, and making use of scanning software to do so is a great idea.
For network administrators, having network scanning software installed allows them to carefully check whether all hosts are working properly or not, and make sure that the network continues to perform smoothly.
The most important thing to keep in mind here is the fact that the network must be stable and perform well enough in order to ensure that effective communication and connectivity is provided to all users.
Hence, network scanning software is able to utilize different tools in order to keep the network running smoothly.
Network security is of vital importance in this day and age.
With so many hacking software programs and scripts available, anybody whose running a network has to make sure that they are able to secure their networks from further damage.
Using a network security scanning software can do just that.
Network security scanning software programs are designed to scan carefully through all of the different hosts and vulnerabilities on a network and then come to a decision whether they pose a risk or not.
Network security scanning software tools are primarily created in order to scan and provide suggestions which could be used in order to strengthen the network further and make it more robust in terms of security.
These programs are available online, and some are specially designed for companies.
With so many different programs available in the market, it is important to carefully research before you opt to purchase one.
It is advised that you talk to professionals who are already working within the network security industry, and get an idea regarding the best programs that can be used.
Once you have a clear picture, only then should you proceed to buy.