With the SecPoint® Protector™ UTM VPN Firewall, you can shield your entire network using state-of-the-art Next Generation Firewall technology. It blocks malware exploits, features robust web filtering, a powerful multi-engine antivirus, and up-to-date anti spam

Highly powerful 64-bit, multi-core architecture
Optimize your traffic and prioritize it efficiently with the Bandwidth Management module
Web Proxy and Web Filtering with Active Directory integration
Top-tier antivirus scanning with multiple engines for the most comprehensive coverage
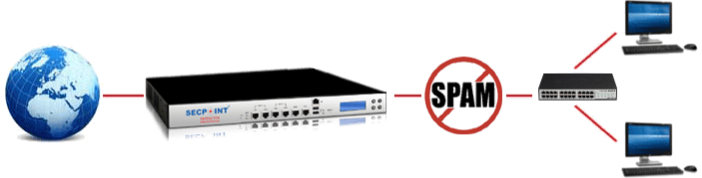
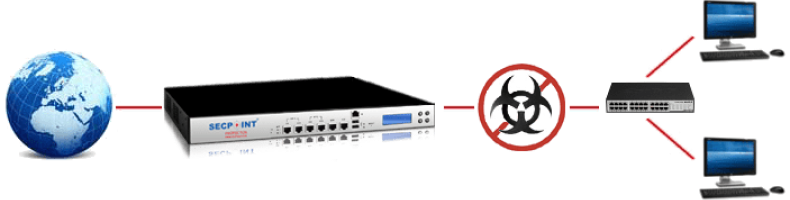
The SecPoint® Protector™ is a 'unified' solution, consolidating services that are traditionally standalone into one feature-rich device
With the UTM protection scheme of the SecPoint® Protector™, you won't encounter the typical challenges. Each software and app within this appliance has been meticulously developed to work harmoniously. They focus on their designated threats without interfering with each other. This cohesion is pivotal as it minimizes the chances of system resources being overtaxed due to conflicting security programs. UTM stands out as the ideal solution for efficiently managing your security measures and defender apps

The SecPoint® Protector™ is a comprehensive UTM (Unified Threat Management) solution that offers robust email threat protection. It is equipped to halt a wide range of threats, including viruses, Trojans, spyware, and other forms of malware. By integrating with the ESET and ClamAV anti-virus engines, SecPoint® ensures top-tier virus protection.
Support for IMAP, Webmail, and POP3 - Multi-layer Email Protection. SecPoint® Protector™ Firewall includes: - Wireguard VPN with IPsec, 0, and 3des-md5 - Client-to-LAN VPN with PPTP and L2TP IPsec.
With Advanced Anti-Spam, you receive state-of-the-art full scanning capabilities. You can easily release emails from quarantine and view their contents.
Automatic heartbeat synchronization ensures High Availability. Connect multiple SecPoint® Protector™ units together for enhanced stability and security. If one unit fails, another can automatically assume the role of the master unit.
Automatic heartbeat synchronization ensures High Availability. Connect multiple SecPoint® Protector™ units together for enhanced stability and security. If one unit fails, another can automatically assume the role of the master unit.
SecPoint® is working in partnership with WifiGem. With it, you can easily create your own Guest Network using one of the available network schemes, and use the SecPoint® Protector™ to filter and prioritize Internet traffic from devices connected to the WifiGem Captive Portal.


An Anti-Spam dedicated appliance can reduce server load. When the email reader's anti-spam filter detects spam, it relocates it to a designated folder, allowing users to either browse or ignore as they see fit.

An anti-virus is a protective software designed not only to defend against viruses but also to detect and remove spyware, adware, and other programs that might disrupt or degrade the user's computing experience, whether they're intentionally malicious or not.

The most effective way to ensure your files remain safe is to maintain a backup on a completely isolated system, like an external hard drive, that isn't connected to the internet. Read more info

We specialize in addressing every threat, ensuring you have a consistent, high-quality software defense.