The Scan Distribution feature has been revised and improved.
This feature makes possible to distribute a vulnerability scan over a number of remote Penetrators, to speed up processing and take benefit from all the available licenses.
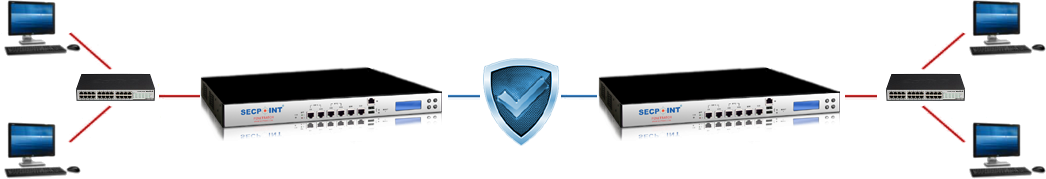
It requires that one Penetrator is configured as Master and one or more Penetrators as Node Client.
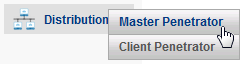
To properly configure the Scan Distribution, you should first configure the feature on the Node Client Penetrator.
Go to menu Distribution > Master Penetrator and click to add a Master Penetrator.
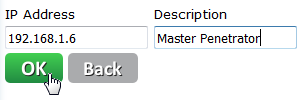
Then enter the IP address of the Master Penetrator, a description and click OK.
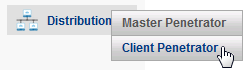
On the Master Penetrator, go to menu Distribution > Node Client Penetrator and add the IP address of the Node Client Penetrator and a description.
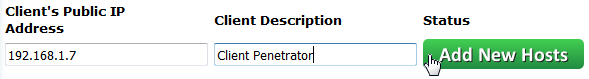
The Master Penetrator will check for the presence of the Node Client and, if it’s available, the Status will be OK.
Starting a scan on a remote Penetrator
When Node Client and Master have been configured, starting a scan on a remote Penetrator is straightforward.
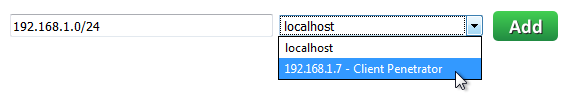
In the Master Penetrator, go to Vulnerability > New Vulnerability Scan, enter the Scan name and click Next.
In the next page, enter the host name or the IP address(es) you want to scan, and, in the next field, choose the Node Client Penetrator where the scan will be performed.
You can also set the advanced parameters in the Advanced Setup page as you would do for a local scan.
![]()
In the same scan It is also possible to mix IP addresses to be scanned on the local and on the remote Penetrator, or even remote scans to be performed on different Node Client Penetrators.
When a Distributed scan is running, the Node Client Penetrator will periodically send information to the Master Penetrator about the count of vulnerabilities found so far on each target.
![]()
This count is visible in the Master Penetrator as for local scans.
Detailed information on the vulnerabilities, though, is only available when the scan is complete.
Therefore the Snapshot functions are not available while the scan is running, and if you try to get a snapshot, the following message is displayed.
![]()